Chrome tab groups are live in Canary on Android
We've known for a while that the Chrome team was working on tab groups. The feature first showed up in Canary on the desktop, but it's now made its way to Android, also in the Canary channel. It's hidden behind a flag though, and works... sort of.
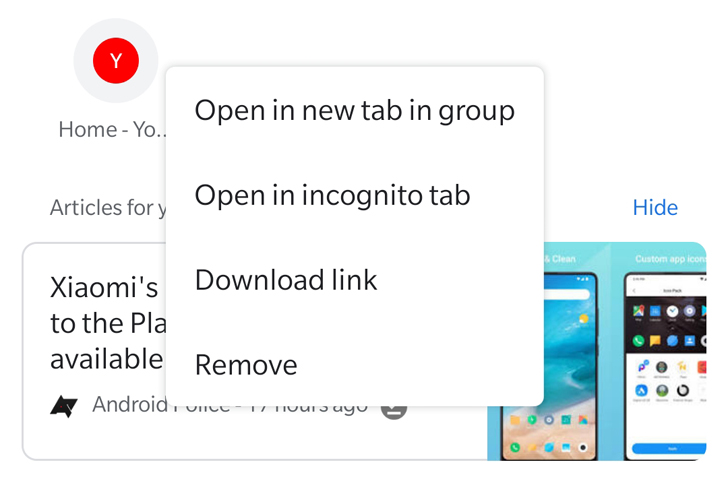
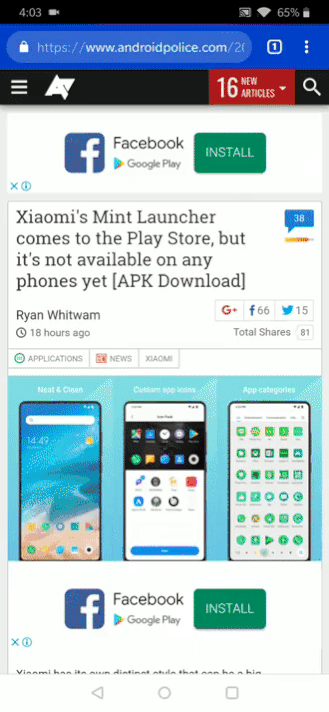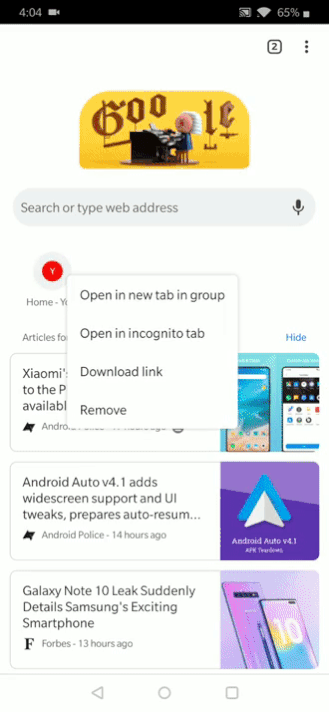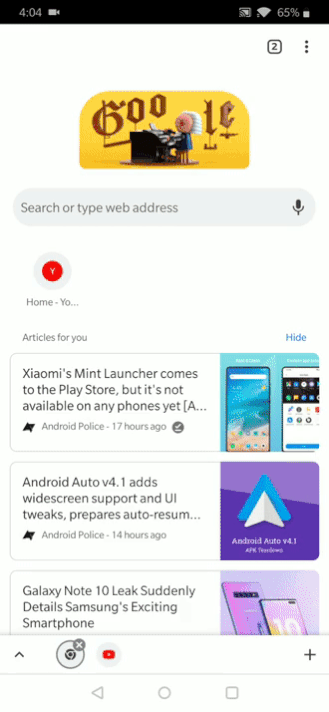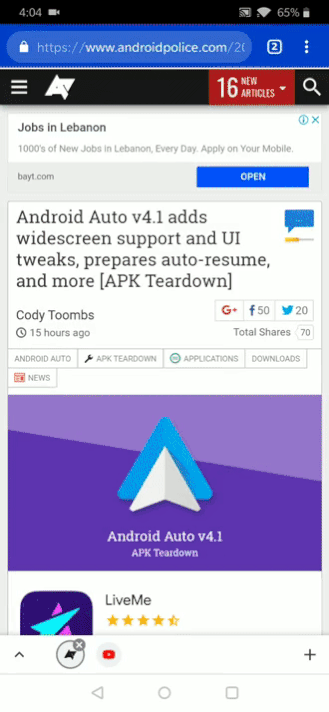
The "Tag groups" flag (found at the URL chrome://flags/#enable-tab-groups) lets you enable groups. The only way to trigger them now is to open a new tab and tap and hold on any icon in the recommended sites. You'll see the "Open in new tab in group" option. A new bottom menu (which is the weird interface we covered a while back) will appear, and this is where the tabs belonging to this group reside. You can switch between them, open a new tab, and expand the menu to view tab thumbnails and close them.
Left: Opening in a new tab group. Right: Switching between tabs in a group.
The feature is still unfinished though. When you access the regular tab switcher, the group is only represented by the last tab you viewed in it. There's no stack of cards, for example, to show that this is a group, which can get very confusing.
With the latest Chrome Canary v75.0.3748 (APK Mirror), tab groups have received a couple of improvements. First, there's a new button to create a group in the grid tab layout. So instead of having to go through a link on the home page to do it, you can now easily start a group from the switcher. Second is that a tab group is represented by a grid of mini thumbnails, and the number of tabs inside is clear.
Left: Create group from the tab switcher. Right: Tab groups show mini thumbnails now.
Finally, one last improvement was discovered by our tipster, Nick Cipriani. You can now swipe any of the tabs or groups away (left to right) in the switcher. This feature was missing when the grid layout was introduced. Tapping the small close button was certainly more annoying than a simple swipe.


Comments
Post a Comment